Back in early 2019, I discovered a remote command execution vulnerability in a Perl web application. Yes you read that correctly, 2019 and Perl web application in the same sentence. I'll attempt to reproduce some of the technical details here.
While assessing the application, I found a pretty blatant LFI vulnerability. The application supported a request for a file parameter that would return an arbitrary file to the requesting browser. The normal behavior was something like the below screenshot.
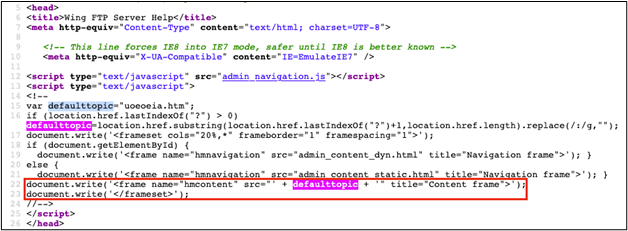
After assessing the file's contents, I quickly was able to find the open() call made by the script and sure enough, it was vulnerable to command execution.
I exploited the vulnerability as shown in the below screenshot by adding a single vertical pipe to the end of a known executable file, such as /usr/bin/id.
Long story short: its now 2021, lets stop using Perl CGIs in web applications.
Reference:
Dimov, Jordan. Security Issues in Perl Scripts, www.cgisecurity.com/lib/sips.html.